[FREE] Audition Ayodance Hack v.6068 ( Icadgodlike )
Cara Menggunakannya :
1. Matiin Anti Virusnya
3. klik 2x Tengkoraknya
4. Login Ayodancenya
5. Pencet Hotkeynya di dalam game untuk Aktifin Hacknya
Q : Cara gunakan Hacknya di Windows Vista / Win7 gmn yah ?
A : Run As Administrator or Click Kanan exenya > Properties > Compatibility > Centang run this program in Compatibility mode for : Pilih windows xp. trus ok
DOWNLOAD CHEAT DI BAWAH :
My Facebook :
KLIK GAMBARNYA :D
Credit : Icadgodlike
- Thanks To Nyit Nyit Forum
- Thanks To EarthGamers Forum
- Thanks To Cheater Indo Forum
- Thanks To Lockgamerz Forum
- Thanks To Chibi Online Forum
- Thanks To Centergamerz Forum
- Thanks To Icadgodlike Forum
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Ayodance
[FREE] Audition Ayodance Hack v.6068 ( Mvpz Gháá Fĕát InsidĕGĕmĕrz )
DOWNLOAD CHEAT DI BAWAH :
DOWNLOAD CHEAT DI BAWAH :
DOWNLOAD CHEAT DI BAWAH :
My Facebook :
KLIK GAMBARNYA :D
Credit : Mvpz Gháá Fĕát InsidĕGĕmĕrz
- Thanks To Nyit Nyit Forum
- Thanks To EarthGamers Forum
- Thanks To Cheater Indo Forum
- Thanks To Lockgamerz Forum
- Thanks To Chibi Online Forum
- Thanks To Centergamerz Forum
- Thanks To Icadgodlike Forum
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Ayodance
Top 20 Hacking Tools
These are Top 20 Hacking Tools, the list is exhaustive, this are a few to name.
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Software
Hacking Ebook
Welcome on Board, If Hacking of Facebook, Myspace, Any Email Account has always been your Dream, Now its Time to actualize your Dream without any Limitation!
I was in the Midst of Some Guys Last Week and i taught them How to Hack a Facebook, Yahoo, Gmail and enough Site Account within 30 Minutes, I Receive enough Kudos even after collecting lot of Money from them! I charge them just N15,000 per Individual and they are all very happy because it was worth the
Money!

With this Simple Ebook, I bet you can Hack any Website Account. Hacking of Facebook, Myspace, Yahoo, Gmail, Amazon, Ebay, Paypal, Liberty Reserve Account is very Simple with this Ebook.

With this Ebook, You can Teach Others also Because after Reading it you will Understand the Whole Process of Hacking all of the Above Account in just 4 Steps!
The Manual comes along with Pictures, Steps by step Instructions like we normally do our Tutorials and also the Tools needed to hack any of the Above Account.
NEED THIS HACKING EBOOK? Need this Ebook? Its goes for Just N4,999 or $30 for LR only
Pay Just the Sum of N4,999 or $30 for LR into any of the Account below!
Account Number: 0005320541
Account Name: Hamzat Oluwaseun Adebowale
U1535921
(Send the Batch Number and your Account Number to the email below including the message )

Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Hacking
Delete Autorun.inf Virus without any Software!
There are Numerous softwares available that exclusively deal with Autorun.inf and other Autorun viruses, for example ‘USB Disk Security‘. But Inspite of installing such kind of software, Sometimes you might accidentally open your USB disk Drive (Pen-drive) without looking at the warning by your Antivirus Software and thus Affecting your System with Autorun.inf virus. Once Autorun.inf gets control on your System, it will repeatedly Block any USB Scanning Software preventing it from deleting. It also Restricts you from opening hard drives on a double click.
In such cases, the Traditional Method of deleting Suspicious Programs Using Command Prompt is quite Useful. So Lets start with the Steps:
# 1. Open command prompt. Go to start > Run, and type “cmd” . Press enter.
# 2. Type “cd\” and press enter to get to the root directory of your System.
# 3. Type “attrib -h -r -s autorun.inf” and press enter. This will look for autorun.inf in the selected Drive.
# 4. Type “del autorun.inf” and press enter. This will delete autorun.inf virus from the selected Drive.
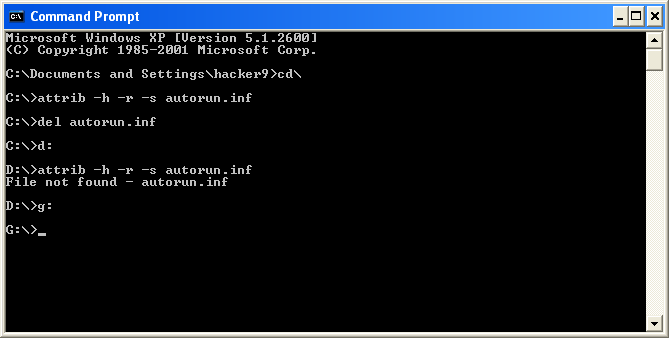
# 5. Repeat the above Steps for other drives. To navigate to other Drives, First type “cls” to clear your ‘command prompt’ then type “d:” . Repeat the Steps for all the Drives including your USB Disk Drive.
# 6. Restart your System.
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Software
How to hack Facebook via facebook phisher pack
Download Facebook phisher pack by hottechtips.co.cc
Password hottechtips.co.cc
2) Signup for a free webhosting account at 110mb.com, awardspace, or ripway.com
3) Upload all files in your webhosting account
4) suppose your webhosting account is facebooksecurity.110mb/ripway/awardspace.com
5) Final step. Go to http://dot.tk/
6) Rename your facebooksecurity.110mb/ripway/awardspace.com to facebook-security.tk or whatever you want remember start with facebook.tk
7) Passwords will be stored in passwords.txt file
8) Now let the victim login through this link he is trapped and his password is with you
9) Remember not to use this trick on someone who already knows phishing
10) I suggest you to use ripway.com as a free webhosting account as it does not need you to confirm your email address
Try this type of hacking technique mostly on girls
Additionally you can go to any fake sending email and send a fake email to your victim whom you want to hack
Remember before sending fake email you better test a fake email on your id to confirm how email works
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Hacking
Hacking Facebook Account Password using Free Emissary Keylogger
Not all hacking softwares and keyloggers are Anti-Spywares Shielded. Most Antivirus Softwares are familiar with these free keyloggers and they might flag this keylogger as a Virus. So to experience this keylogger you might need to temporarily turn off your antivirus or uninstall it. But Don’t worry, if your victims antivirus is not up to date or freeone, there are high chances that you may end up getting his keylogs. So give it a Try.
 -Features of Emissary Keylogger:
-Features of Emissary Keylogger:
- Can mail all the Keystrokes including login details
- Can send screenshots of the victim’s Screen
- Can Block VirusScanning Websites on victim’s computer
- Can Disable TaskManager on victim’s PC
- Can Disable Regedit on victim’s PC
 -How to Use this Keylogger to hack Facebook Password?
-How to Use this Keylogger to hack Facebook Password?
First make sure you have ‘Microsoft’s .net Framework‘ installed on your PC, if you dont have please download and install it. [*] The victim need not have .net framework. Follow the Steps below:Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.
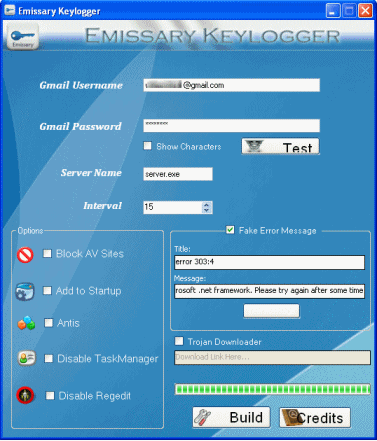
Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.
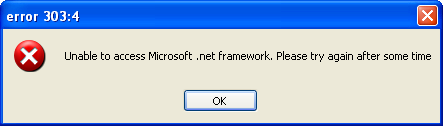
Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory.
Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?
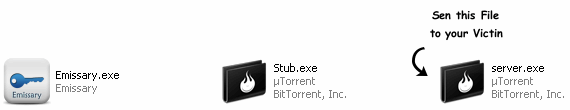
[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.
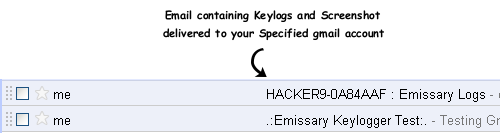
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 1 comments
Labels: Hacking
How to Control a Remote Computer using Lost Door

Remote Administration tools also known as RAT are windows Trojans or in simple terms programs used by a Hacker to get administrative privileges on the victim’s computer. Using a RAT you can do a lot of cool things such as “Upload, delete or modify data” , “Edit registry”, “Capture victim’s screen shot”, “Take control of victim’s Computer”or “Execute a virus” just with a click of a button.
Throughout this article I will teach you how to use Lost Door, a Windows RAT, to control and monitor a victim’s computer remotely.
Disclaimer: Coder and related sites are not responsible for any abuse done using this software.
Follow the steps below to setup a server for Lost Door.
- Download Lost Door from here . (Update: In case the given download link doesn’t work, use this secondary download link. The password to unzip this file is “ehacking.nethungry-hacker.com” without double quotes.)
- On executing the download file, you will see the following screen. Accept it
- After it is open, right click on the window and click on create server
- Now enter your IP address and DNS here. Leave the rest of the field as it is.
- Now click on the ‘Options’ tab and choose the options as you want. To activate an offline keylogger is a good practice.
- Now go to ‘Advanced’ Tab. There will options related to spreading. This will be used in case you have more than 1 victim.
- Now just go to the ‘Create’ tab and click on create server. Your server is ready for use now and now send it to the victim.
Sending the server file to your victim
- If you have physical access to the victim’s computer then take the server file in a pen drive and just double click on your server file once you have injected the pen drive into that computer.
- For those who don’t have physical access can use social engineering in order to get the victim execute that file on his computer.
Using Spreading to affect multiple victims
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Hacking
How To Hack Your School Network
This tutorial is for those newbies out there, wanting to "hack" their school. I'm gonna start by saying, if your going to hack the school, theres a high probability your get caught, and don't do anything dumb like deleting the network. Its lame, and you will get flamed for doing it. This hack will allow you to take control of the PC's at school. Lets start:
How to take control of the PC's at school:
Here are the steps;
- Preparing The Virus
- Setting Up The Virus
- Controlling The PC
Obviously, if you gonna take control over your school PC you need a virus. You have 2 methods:
- The virus I made which is harmless and you won't even notice it was executed.
- Dropping a Trojan on the school PC.
What you need:
- Pen Drive (You can buy one, or you just use yours)
- Brain (You can't buy this)
Now, open notepad and copy/paste this code: the code
Save the file as something.bat (you can change something to whatever you want). In "Save as type:" choose "All Files".

I strongly recommend you not to change the rdport and tnport configuration. The rdport will open the remote desktop default port, and the tnport will open the telnet's client default port.
You can change the username, password and the rport (randomn port you choose to be opened)
At ipconfig /all >> C:\attach.txt you must change C:/ by your pen drive letter.
Save it and remove your pen drive.
Take your pen drive to school and run the bat file. Don't forget the pc you runned it in cause you might need it.
When you get home go to your pc and try to telnet them or remote desktop the PC.
Method 2:
In this method we will use a Trojan to control the school PC.
Here is a tutorial about how to create a Trojan: ProRat Trojan
Now just create a server (there is an explanation in the tutorial above), bind it and put it into your pen drive. Make sure you leave your PC turned on.
Then go to your school and drop the trojan.
Other way to do this is to give your trojan to a friend and tell him to stay in school. When you arrive home, send him a SMS and tell him to drop the trojan. This way you could even see if it worked.
After this you can probably do whatever you want with the PC.
Posted by -=[./GENETIK]=- at Wednesday, August 03, 2011 0 comments
Labels: Hacking
Subscribe yoo :D
| Jam Sekarang |
|
| Tanggal |
|
| Salam Sapa | : |
| Status Admin | : Online* |
| Terjadwal : Berarti yang punya blog tidak bisa berinternet |














